SSH (Secure Shell)

SSH (Secure Shell) is a network communication protocol that enables two computers to communicate in a secure way. SSH uses both password authentication and public key authentication. Typically, user authentication is done through public key authentication. After user authentication is done, SSH shifts to password authentication.
Public Key Authentication
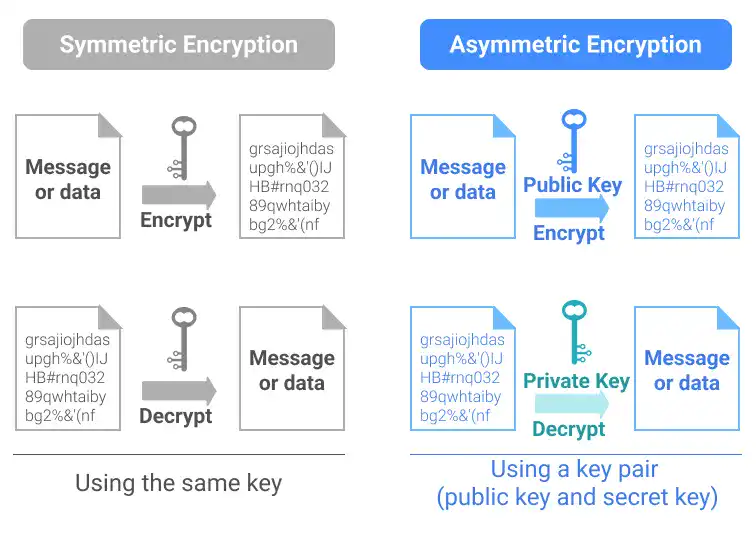
While conventional encryption technology uses only a single key for both encryption and decryption (Symmetric Encryption), Public-key Authentication uses a key pair (Private Key and Public Key for Asymmetric Encryption). In Public-key Authentication, a public key can be shared with anyone while a private key is kept secret (a private key is also called a secret key). The encryption of a message or data is done with the public key, and only the private key can decrypt the message or data.
SSH use cases – Remote Login and Secure File Transfer
There are two major use cases for SSH – Remote Login and Secure File Transfer. SSH remote login is widely used to manage servers remotely. It is also used for several cloud services such as AWS, Azure, and GCP. You can use SSH to connect to git remote repository services such as GitHub. SSH is also used for file transfer in a more secure way. There are two major commands for executing file transfer with SSH – SCP and SFTP.





